
Internet Security and Acceleration Server
Internet Security and Acceleration Server
Contents
-
 Introduction
Introduction -
 Product
Overview
Product
Overview -
 Firewall
and Security
Firewall
and Security -
 Caching
and Acceleration
Caching
and Acceleration -
 Secure
Internet Connectivity
Secure
Internet Connectivity -
 Extensible
Open Platform
Extensible
Open Platform -
 Questions
Questions -
 Conclusion
Conclusion
Introduction
You may not have heard of the Internet Security and Acceleration (ISA) Server, but likely you heard of its predecessor. ISA Server is both a new product and a revised release of Microsoft Proxy Server 2.0. In a move to reposition the product and to avoid confusion with its competitors, such as Netscape, they renamed the product. ISA Server is new in that it is based on the security and reliability features of the Microsoft Windows 2000 operating system and has a new architecture designed for firewalling and caching. The ISA Server's robust firewall and caching features provide performance and security enhancements to networks and support scenarios where you previously did or would use Proxy Server 2.0.
Why the need for ISA Server? Well there is no question the Internet provides organizations with new and exciting opportunities to connect with customers, suppliers, partners and employees. While this presents great opportunities, it also opens up an organization to new threats and concerns such as security, performance and manageability. Microsoft designed ISA Server to address the needs of today's Internet-enabled businesses. ISA Server provides a multi-layered enterprise firewall that helps protect network resources from viruses, denial of service attacks and unauthorized access. And ISA Server's Web cache enables organizations to optimize network bandwidth and provide accelerated Web access for its clients by serving objects locally rather than over congested networks.
Whether deployed as a dedicated firewall or as an integrated firewall and caching server, ISA Server provides a unified management console that simplifies security and access management.
Product Overview
Internet Security and Acceleration Server 2000 provides secure, fast, and manageable Internet connectivity. ISA Server integrates an extensible, multi-layer enterprise firewall and a scalable high-performance Web cache. It builds on Microsoft Windows 2000 security and directory for policy-based security, acceleration, and management of internetworking.
ISA Server comes in two editions-Standard Edition and Enterprise Edition. Standard Edition is a stand-alone server supporting a maximum of four processors; whereas, Enterprise Edition supports server arrays, multi-level policy, and computers with more than four processors.
ISA Server supports all client platforms through its SecureNAT feature. The ISA Server firewall client is an optional software component for 32-bit Windows-based clients (Windows 3.9x, Windows Millennium Edition, Windows NT Workstation, and Windows 2000 Professional) that adds user-level authentication and support for additional protocols without requiring application filters. The Hypertext Transfer Protocol (HTTP) client is supported by any CERN-compatible browser (such as Microsoft Internet Explorer or Netscape Navigator) and, with the HTTP application filter, any client application using HTTP to access the Internet.
Simplistically, the rich feature list of the Internet Security and Acceleration Server includes:
- Enterprise firewall: ISA Server 2000 serves as a firewall, providing secure Internet communication by preventing unauthorized network access.
- Web caching server: ISA Server 2000 maintains a centralized cache of frequently requested Internet objects that all ISA Server clients can access.
- Unified management: ISA Server 2000 supports Active Directory, Microsoft Management Console, Windows 2000 Terminal Service and other support tools or standards.
- Extensible platform: \tab ISA Server 2000 includes a comprehensive software development kit and application programming interfaces (APIs) to help developers create extensions to meet custom security or administrative requirements.
Firewall and Security
As mentioned already, ISA Server 2000 is both an integrated firewall and caching solution, and a locked-down firewall or dedicated cache. During the setup process, you can select the ISA Server mode: firewall, cache, or integrated. In firewall mode, you can secure network communication by configuring rules that control communication between your corporate network and the Internet. You also can publish internal servers, securely sharing data on your internal servers with Internet users. In cache mode, you can improve network performance and save bandwidth by storing commonly accessed objects closer to the client. You also can publish internal Web servers. Integrated mode combines the features of both firewall and cache, ensuring security and enhancing performance. In all modes, you can benefit from ISA Server enterprise policy management, real-time monitoring, and reporting features.
When deployed as a dedicated firewall, ISA Sever acts as the secure gateway to the Internet for internal clients. The ISA Server computer is transparent to any party in the communication path. The Internet user cannot tell that a firewall server is present, unless the user attempts to access a service or site where the ISA Server denies access.
ISA Server Rules
By configuring rules, administrators can help prevent unauthorized access and malicious content from entering the network as well as restrict outbound traffic by user, group, application, destination, content type and schedule. ISA Server allows administrators to define three types of rules:
- Access policy rules
- Bandwidth rules
- Publishing rules
Access Policy Rules
Organizations can use ISA Server to configure an access policy consisting of site and content rules, protocol rules and IP packet filters.
Site and content rules define Internet sites accessible by clients behind the ISA Server computer. Site and content rules are processed at the application level.
Protocol rules define the protocols users behind the ISA Server computer can access. Protocol rules are processed at the application level.
IP packet filters allow or block communication between specified IP addresses, using the specified protocols and ports. IP packet filters are processed at the packet level.
Bandwidth Rules
ISA Server bandwidth rules build on the Windows 2000 features to determine how much bandwidth to allocate for any specific Internet request. Bandwidth rules are processed at the application level.
Publishing Rules
Server publishing rules filter all incoming and outgoing requests. These rules map incoming requests to the appropriate servers behind the ISA Server computer. Web publishing rules map incoming requests to the appropriate Web servers behind the ISA Server computer.
Caching and Acceleration
Most Web browsers feature local caching of objects, where requested Web pages are stored after retrieval in a computer's local cache. ISA Server improves upon this concept by maintaining a centralized cache of frequently requested Internet objects accessible by all ISA Server clients. HTTP and FTP objects served from ISA Server's memory or disk cache require substantially less processing than objects served from an external network, such as the Internet. The Web cache is built on top of the Web proxy engine, which provides HTTP connectivity, filtering, content screening and URL blocking.
When deployed as a caching server, ISA Server improves client browser performance, decreases user response time and reduces bandwidth usage on Internet connections. Caching reduces bandwidth requirements by moving Web content closer to the user. Microsoft reports that caching frequently requested content can decrease bandwidth usage by as much as 40 percent. Caching also can provide content to users even when the content source is offline or otherwise unavailable. The scheduled download of cache content allows ISA Server to update the cache with HTTP content that Web proxy clients may soon request . When used wisely, scheduled content download saves valuable network bandwidth and improves the overall cache performance without affecting throughput. Since the ISA Server scheduled cache content download service is a Windows 2000 service; it can be stopped, started or paused like any other Windows 2000 service.
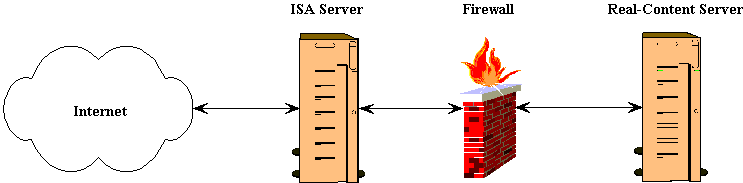
Reverse Web Caching Server
Reverse caching means placing a cache in front of a Web server or e-commerce application. It is called "reverse" because it is implemented by the administrators of the Web servers, rather than by the clients, to cache or distribute content from the servers or to offload processing. ISA Server supports reverse caching , allowing Web managers to cache and distribute content, thereby improving user response time. Figure 1 depicts reverse caching.
Figure 1 Reverse proxy.
ISA Server can be deployed in front of an organization's Web server that is hosting real Web content. With incoming Web requests, ISA Server can act as a Web server fulfilling client requests for Web content from its cache and forwarding requests to the Web server only when the requests cannot be served from its cache. Figure 2 demonstrates this security measure.
Figure 2 Sever proxying.
Forward Web Caching Server
You can deploy ISA Server as a forward caching server that provides internal clients with access to the Internet. ISA Server maintains a centralized cache of frequently requested Internet objects accessible by any Web browser. Again, objects served from the disk cache require significantly less processing than objects served from the Internet. This improves client browser performance, decreases user response time, and reduces bandwidth consumption on Internet connections.
Distributed Caching
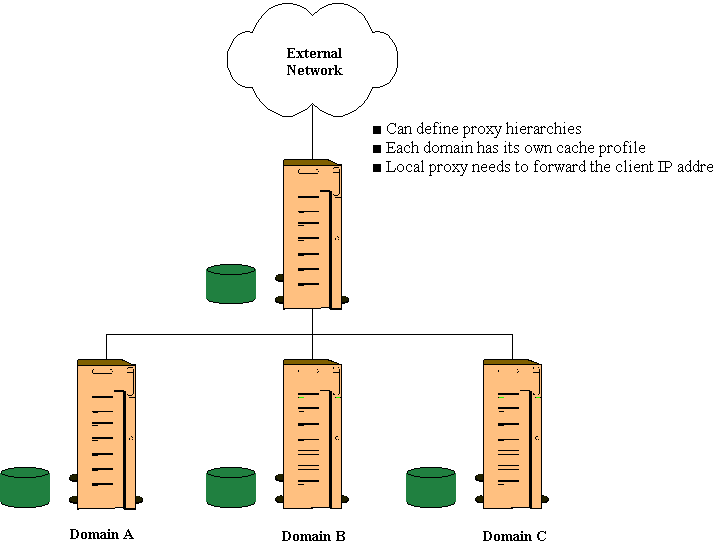
One of the most powerful feature sets in ISA Server is its support for distributed caching. ISA Server Enterprise Edition allows distributed caching using multiple ISA servers chained together in an array. Distributing the cache load allows scaling beyond what a single server can provide, balancing the load, and providing fault tolerance when a cache server is unavailable. Distributed caching can be implemented with arrays, chains, or a combination of both. Figure 3 shows combination distributed caching. ISA Server Enterprise Edition uses the Cache Array Routing Protocol (CARP), a scalable, efficient, and flexible architecture that allows multiple servers to act as a single cache without duplicating content.
Figure 3 Combination distributed chaining.
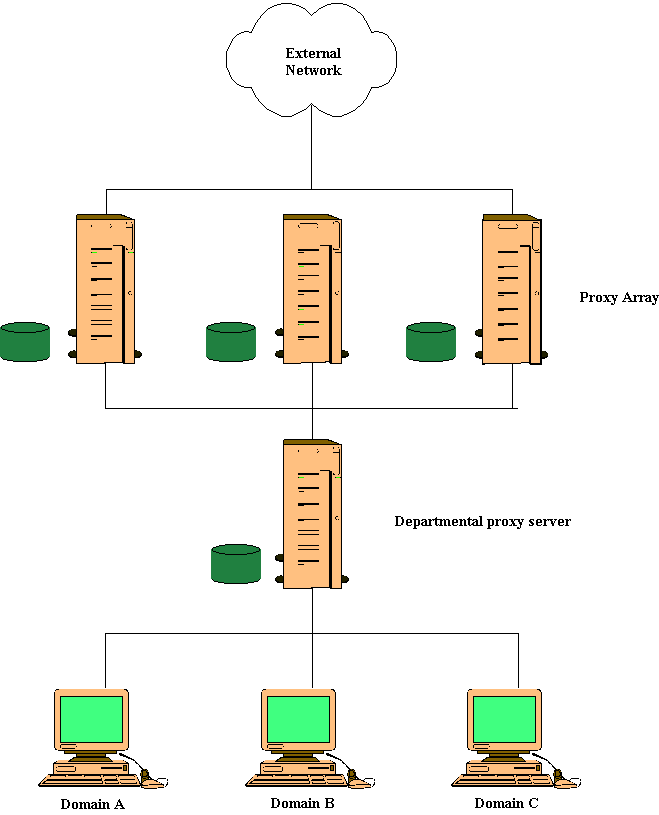
Distributed caching is important because it allows caching to take place closer to users. For example, within your enterprise, cache chaining can move beyond a single, central location at the edge of an organization's network and toward the branch office and workgroup levels. Moving the caching closer to the user again reduces network traffic and improves performance. And equally consequential, it also reduces cost. These factors become even more important as organizations deploy support for content distribution technologies.
Chained or Hierarchical Caching
Chaining is a hierarchical connection of computers running ISA Server. Requests from clients are sent upstream through the chain until the requested object is found. For example, a client request in a branch office would go to the branch office ISA Server, then on to the divisional, regional or corporate headquarters before sending the request to the Internet.
ISA Server computers can be chained as either individual computers or as arrays. Chaining is also an effective means of distributing server load and fault tolerance. Secure sockets layer (SSL) chaining is also supported.
Secure Internet Connectivity
Connecting networks and users to the Internet introduces security and productivity concerns. Internet Security and Acceleration Server offers features that let you control access and monitor usage. ISA Server protects networks from unauthorized access, inspects traffic, and alerts administrators to attacks.
ISA Server includes an extensible, multi-layer enterprise firewall that includes things like security with packet-, circuit-, and application-level traffic screening, stateful inspection, broad application support, integrated virtual private networking, system hardening, integrated intrusion detection, smart application filters, advanced authentication, and secure server publishing.
In scenarios where specific routing has to be established for ISA Server use, you can configure connectivity between local area networks with PPTP and L2TP. For all purely routing-related functions, there is no collision between ISA Server and RRAS features. However, Microsoft recommends that one only configure secure network address translation (SecureNAT) and dynamic packet filtering functionality through ISA Server and not through RRAS. ISA Server allows for dynamic packet filtering where the required ports are opened and closed based on client requests. This makes for a more secure firewall because ports are not left open unless absolutely required to support services in use on the network.
ISA Server helps you set up and secure a virtual private network. Using wizards, ISA Server can configure the built-in VPN services of Windows 2000 Server, helping organizations achieve cost-effective links for remote sites and mobile users. ISA Server supports VPNs in two ways. One is allowing VPN connections to and from the ISA server itself. This is done by enabling the PPTP call and receive filters, which statically open the required ports to make outgoing calls (PPTP call) and incoming PPTP requests (PPTP receive) directly to and from the ISA server. The other way ISA Server supports VPN is by allowing clients to initiate VPN calls from behind the ISA Server to hosts on the Internet or the external network.
When an ISA Server is present on the packet route path of any client on any platform, ISA Server transparently intercepts the traffic and applies policy to it. SecureNAT applies outbound firewall policies without the need for installing client software or re-configuring browser settings.
ISA Server supports encrypted content at several levels. ISA Server can help you set up a secure, encrypted VPN channel to remote networks. The channel then can transport any data in a secure manner . ISA Server can enforce the use of encrypted Web access on incoming Web requests and can serve as an end point of an encrypted SSL session.
ISA Server allows organizations to publish services to the Internet without compromising the security of their internal network. They can configure Web publishing and server publishing rules that determine what requests should be sent downstream to a server located behind the ISA Server computer, providing an increased layer of security for their internal servers. For example, you can place a Microsoft Exchange server behind the ISA Server and create server publishing rules that allow the e-mail server to be published to the Internet. Incoming e-mail to the Exchange Server is intercepted by the ISA Server computer , which appears as an e-mail server to clients. ISA Server can filter the traffic and forward it on to the Exchange Server. The Exchange Server is never exposed directly to external users and remains in a secure environment, maintaining access to other internal network services.
Extensible Open Platform
Security policies, and directives, vary from organization to organization. Traffic volume and content formats also pose unique concerns. Since no one product fits all security and performance needs, Microsoft built Internet Security and Acceleration Server to be highly extensible. ISA Server includes a comprehensive SDK that includes full API documentation and samples of filters and administration extensions that enable your organization to address specific security and performance concerns. These components include Web and application filters, management tools, user interface extensions, and more.
A growing number of third-party partners offer functionality that extends and customizes ISA Server, including virus scanning, management tools, content filtering, site blocking, real-time monitoring, and reporting. Customers and developers have the ability to create their own extensions to ISA Server.
Questions
Planning
- Is there a business plan for the project that implemented ISA Server?
- Does the business plan adequately address the organization's needs?
- Is the hardware and software consistent with the organization's technical platform?
General Configuration
- Does your Web site or proxy have a published privacy policy?
- How was ISA Server configured?
Firewall Cache Integrated
- How many users will be passing through the firewall at peak usage?
- Is the ISA Server adequate to support the maximum number of users?
- Do proxy programs support challenge-response authentication or third-party security schemes?
- Does it support Kerberos?
- Does it support NTLM?
- Does it support basic authentication?
- Does it support anonymous browsing?
- Are password controls implemented (e.g., format, aging, etc.)?
- Has a secure password policy been implemented? Is it enforced?
- Can users be put into access groups for the purpose of setting up access rules?
- Can the ISA Server be managed locally at the console?
- Is remote Telnet access necessary for remote maintenance?
- Is remote maintenance secure?
- Does the firewall provide different levels of administrative access to the firewall for two levels of users (e.g., systems administrator and assistant)?
Proxy Logs
- Have the ISA Server logging requirements been defined?
- Have you configured logging?
- Is logging by packet, bytes transferred, source and destination?
- Is logging by service used?
- What is the policy regarding logs? Record nothing? Record nothing, anonymize the outgoing request? Record everything, analyze nothing? Record everything, analyze everything?
- Do you use all the log information you collect?
- Does the server provide statistical data?
- Is usage billing and accounting provided?
- Is log data exported to a secure log server?
- Are server log files protected against snooping?
Alerting
- Can audit alarms (e.g., e-mail, logging, SNMP traps, pagers) be configured for predetermined security events?
- Have you configured alerts to inform you of suspicious network events, such as frequent protocol violations, SYN or FRAG attacks, or dropped packets, which can signal an attack?
Basic Security Considerations
- Is IP forwarding disabled?
- Is access control enabled?
- Is this based on user names?
- Is this based on source/destination IP network addresses?
- Is the firewall configured to prevent IP spoofing attacks where packets arriving from external networks appear to come from internal networks?
- Is the firewall configured to prevent IP spoofing attacks where packets arriving from internal networks appear to come from external networks?
- Is membership to the Administrator group limited to only the administrators who require such access?
- Are user rights limited?
- Are strict Windows 2000 account policies enforced?
- Does the Local Address Table (LAT) consist only of internal IP addresses?
- Have all network drive mappings to other remote computers been removed from the ISA Server computer?
- Are FAT volumes used on the ISA Server computer?
- Have you disabled the ports used for Remote Procedure Call (RPC) listening on the Internet interface?
- Have you double-checked the permissions set on any shares created on the system where you are running ISA Server on your Internet adapters?
- Have you stripped the ISA Server computer to only the services and applications required?
- Is ISA Server and Internet Information Services (IIS) running on the same computer?
- Have you disabled unneeded IIS services, such as FTP?
- Are all unused services unbound from your Internet adapters?
- What is cached? Web pages? Passwords and authentication information? Cookies? Expiration dates? Encryption and SSL documents? Failed requests? Keywords?
Packet Filtering
- What Packet Filters are configured? Inbound packet filtering supported? Outbound packet filtering supported? TCP packets? UDP packets? Dynamic? Static?
Circuit Filtering
- Is a generic proxy service (e.g., circuit) needed?
- Can a generic proxy connection be initiated from the external network?
- Can generic proxies be configured to authenticate users with passwords?
Application Filtering
- What applications are supported? Hypertext Transfer Protocol (HTTP)? Simple Mail Transfer Protocol (SMTP)? Post Office Protocol (POP)? Network News Transfer Protocol (NNTP)? File Transfer Protocol (FTP)? Telnet? RealAudio? RealVideo? Internet Relay Chat (IRC)? H.323? Windows streaming? QuickTime? Others?
- Does the firewall screen FTP access through FTP by each FTP command (i.e., GET and PUT)
- Does the HTTP proxy authenticate outbound as well as inbound users?
- Does SMTP proxy merely forward all messages to an internal SMTP?
- If SNMP proxy is provided, does it allow sets to be made through the firewall or up to the firewall?
- Are there any applications that will be used in the future for which the firewall should provide proxy support (e.g., Oracle, Sybase, etc.)?
- Is URL filtering supported?
- Is there a policy for filtering URLs?
Finally, consider these basic security considerations when setting up ISA Server as a firewall:
- Disable RPC
- Disable IP forwarding
- Enable access control
- No external IP addresses in the LAT
- No network drive mappings to remote servers
- Use NTFS volumes
- Keep server simple and secure
- Unbind unnecessary services from network interface
- Remove DNS and gateway references
- Configure alerts
- Configure logging
The Internet has changed the way people and organizations communicate and conduct business. Organizations of all sizes are transforming their businesses by connecting their networks to the Internet. While this presents great opportunities, it also brings new concerns and risks that organizations must address. Microsoft designed ISA Server to meet the needs of Internet-enabled business by providing enterprise security, fast Web caching performance, and powerful unified management tools built for Windows 2000.
ISA Server provides a multi-layered firewall with built-in intrusion detection to keep internal networks safe. The Web Caching feature provides organizations with fast Internet access for their internal employees as well as high-performance e-commerce through reverse caching. The powerful, policy-based management features integrate with Windows 2000 Server, making security and Web caching easier to manage.
ISA Server provides businesses with secure, fast Internet connectivity built on the powerful management features of Windows 2000. Organizations wanting to Internet-enable their networks should consider ISA Server a critical component of their communications infrastructure.
In this paper, you only have seen the tip of the iceberg. You'll need supplementary information to perform an adequate review. Fortunately, there are other helpful sources, such as:
- The Microsoft Internet Security and Acceleration Server Web site ( http://www.microsoft.com/isaserver/) provides the latest news, case studies and product information}}
- The Microsoft Security Web site (http://www.microsoft.com/security/) provides information on security.
Abridged version of a document originally published by Auerbach Publications 2001.